SSDs, encryption and decommissioning
Updated: 2011-02-28 14:00:10
 A research paper about the secure erasure of data on SSDs has raised a lot of discussion.
What steps do you need to take when decommissioning a disk? Read more…
A research paper about the secure erasure of data on SSDs has raised a lot of discussion.
What steps do you need to take when decommissioning a disk? Read more… A research paper about the secure erasure of data on SSDs has raised a lot of discussion.
What steps do you need to take when decommissioning a disk? Read more…
A research paper about the secure erasure of data on SSDs has raised a lot of discussion.
What steps do you need to take when decommissioning a disk? Read more… Will you be in Brisbane, Queensland on Tuesday 01 March 2011? Are you interested in learning about security and meeting a bunch of like-minded people?
If so, why not attend the inaugural meeting of the OWASP Brisbane chapter? (It's free.) Read more…
Will you be in Brisbane, Queensland on Tuesday 01 March 2011? Are you interested in learning about security and meeting a bunch of like-minded people?
If so, why not attend the inaugural meeting of the OWASP Brisbane chapter? (It's free.) Read more… This week the US Department of Health and Human Services levied the first fines under the HIPAA act. Now that they have proven they mean business, other health care organizations need to be sure they have the proper protections in place. Read more…
This week the US Department of Health and Human Services levied the first fines under the HIPAA act. Now that they have proven they mean business, other health care organizations need to be sure they have the proper protections in place. Read more…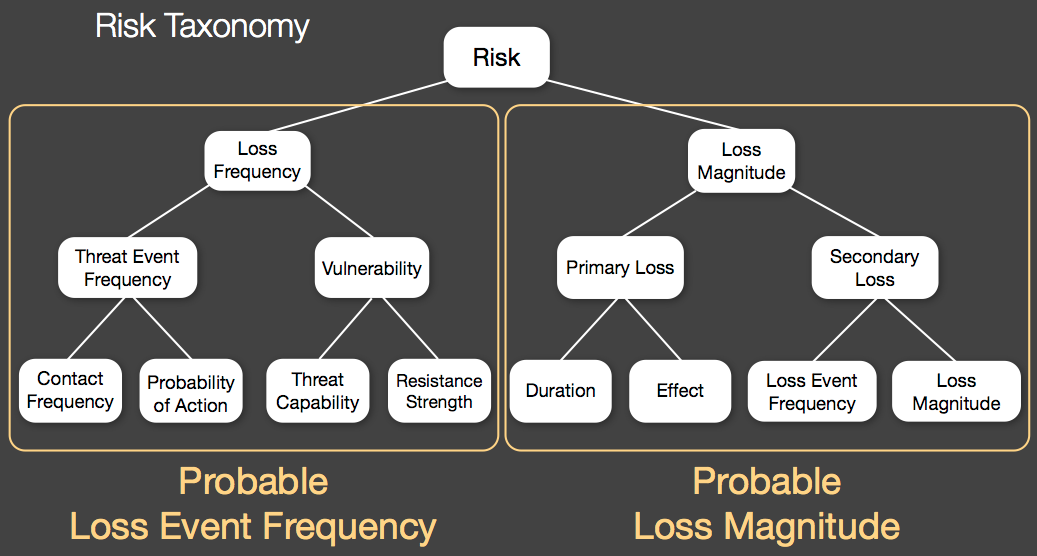 News flash: Those so-called “risk” labels/ratings included in pentest and vuln scan reports are NOT actually “risk” representations. I was in attendance at the OWASP Summit 2011 a couple weeks back, and the topic of “risk metrics” and labels came up during one session. As a result, I led a break-out session on what risk [...]
News flash: Those so-called “risk” labels/ratings included in pentest and vuln scan reports are NOT actually “risk” representations. I was in attendance at the OWASP Summit 2011 a couple weeks back, and the topic of “risk metrics” and labels came up during one session. As a result, I led a break-out session on what risk [...] Greetings from the 2011 RSA Conference in rainy San Francisco, CA. Yesterday I attended the opening keynotes of the conference, and a certain statement by RSA’s Art Coviello caught my ear and needs some further discussion. The conference opened with a fantastic video called “Giants Among Us” which provided a brief chronicle of the rise [...]
Greetings from the 2011 RSA Conference in rainy San Francisco, CA. Yesterday I attended the opening keynotes of the conference, and a certain statement by RSA’s Art Coviello caught my ear and needs some further discussion. The conference opened with a fantastic video called “Giants Among Us” which provided a brief chronicle of the rise [...] Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive February 2011 1 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 240 Corporate 183 Enterprise 314 McAfee Labs 1042 Tags Acquisition Channel Partners Compliance Consumer critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security Endpoint Protection enterprise facebook Family Safety global threat intelligence google government identity protection malware McAfee McAfee Initiative to Fight Cybercrime Mid-Market Mobile mobile security Network Security Operation Aurora PCI
Skip over navigation McAfee® Blog Central Blog Central Corporate McAfee Labs Enterprise Consumer Feeds Podcasts Consumer Blog Feeds Corporate Blog Feeds Enterprise Blog Feeds McAfee Labs Blog Feed McAfee Podcasts McAfee Twitter Feed Archive February 2011 1 January 2011 28 2010 459 2009 398 2008 294 2007 417 2006 169 Blogs Consumer 240 Corporate 183 Enterprise 314 McAfee Labs 1042 Tags Acquisition Channel Partners Compliance Consumer critical infrastructure Cyber Security Mom Cybercrime data breach Data Protection Dave DeWalt DLP Email Web Security Endpoint Protection enterprise facebook Family Safety global threat intelligence google government identity protection malware McAfee McAfee Initiative to Fight Cybercrime Mid-Market Mobile mobile security Network Security Operation Aurora PCI